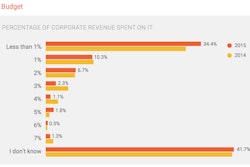
The most-common factor limiting contractors’ technology adoption is very likely lack of budget. Nearly 45% of contractors responding to construction-technology firm JBKnowledge Inc.’s 2015 Construction Technology Study spend 1% or less of their revenues on information technology (across all industries, the average IT spend is 3.5% of revenues). And the JBK study suggests that the second most common excuse for not taking greater advantage of cost reductions and productivity improvements offered by digital management technology may well be concern over security.
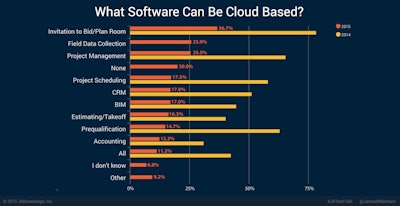
A full 20% of contractors responding to the 2015 Construction Technology Study will allow none of their data to reside on the cloud. Accounting and estimating software is among the least likely to be found on the cloud.
The cloud is where mobile data collection and construction management is making the greatest strides. It’s a key technology at the core of systems revolutionizing construction costs.
“We have an irrational fear of cloud-based systems,” says James Benham, CEO of JBKnowledge. Keeping data out of the cloud is false security. “If it’s digital, I can get it (Benham hacked systems for years as a security consultant).
“It was easier for me to get into clients’ on-premises systems than it was to get into their web-based solutions,” Benham says. “Online solutions had intrusion protection and full-time security staff. On-premises stuff was practically wide open. I could just email the front-desk secretary a picture of a fat cat. She’d click on it to watch the video – people can’t resist videos of fat cats – the link would download a script to her computer that would allow me to take over the whole network.”
Nobody entering competitive bids for construction contracts can afford to ignore the cost-saving, productivity-improving benefits of construction technology based on security concerns.
Technologies may not be sustainable competitive advantages, as competitors gear up with similar technologies, but how you adopt technology can be. Put data security in place before you start digitizing sensitive data, and maintain it as you take advantage of cloud and other digital technologies.
Mike Zusman, president of information security consulting service, Carve Systems (www.carvesystems.com) has identified four data-security risks that all organizations face:
- Phishing. Anti-phishing organization PhishMe (www.phishme.com) estimates that 91% of all data security breaches result from a phishing attack – some sort of social engineering attempt to get into a network by targeting system users. “Your employees are getting phish emails right now,” Zusman says. “It’s not going away, and it’s kind of a hard thing to control. You have antivirus and antimalware, but the attackers adapt. It’s a cat and mouse game.”
- Uncontrolled external network perimeter. Growing use of web applications, internet-of-things devices and machine-to-machine gateways expose companies’ computer networks to the internet. The technologies create a lot of value for contractors, but they come with security obligations. “A lot of organizations don’t know what devices they have facing the open internet,” Zusman says. “They just don’t know what services are running, they don’t know which IPs are live.”
- Insufficient internal access control. “Typically, once a bad guy gets into your network via phishing attack, it’s really, really hard to lock him down and keep him from going anywhere he wants,” Zusman says. “Companies have built their networks around trusting their users, but that rationale falls apart once a bad guy gets his foot in the door.”
- Insufficient security leadership and culture. “Security is a people problem, from the boardroom, all the way down to the mailroom,” Zusman says. “Everybody has to make decisions that will impact security of the organization’s data. But most importantly, senior management needs to be supportive. They need to let the organization know that data security is a priority and devote resources to focus on security.”
Many companies ignore data security. “Organizations are rarely compelled to act unless something bad has happened,” Zusman says. “We see a lot of can kicking: ‘We’re going to address security when we get a new chief technology officer. We plan to hire a director of security to own that.’ Meanwhile time is ticking, and systems are at risk.”
The not-yet-hacked company is an environment where what Zusman calls “faith-based security” can flourish. Decision-makers’ faith in their programmers goes unverified by risk assessment, penetration testing or vulnerability scans. Companies rely completely on marketing claims such as, “Our next-gen firewalls stop advanced attacks!” when almost all security breaches start with phishing that allows thieves to walk right through firewalls with network users’ stolen log-in credentials.
Zusman recommends six steps to getting started with data security:
- Create an information security officer role. “It doesn’t need to be a full-time roll, but somebody in the organization should have ownership over security and risk management,” Zusman says. “They don’t even need to be a security subject-matter expert. But you need somebody to own it and take the responsibility for finding out what security means in your organization.”
Zusman recommends hiring an exploratory risk assessment done by an experienced third-party consultant. “I would definitely suggest looking for a smaller consulting company,” he says. “What we find in our industry is that bigger companies can tend to value managing the business over providing the best services available. When you work with a smaller consulting firm, there’s a better chance that the person who is scoping and selling you the project is going to do the work, or at least managing the work.”
- Have a monthly security meeting. “A good risk-assessment report is going to have action items for you to follow up on,” Zusman says. “You need to have some sort of continual process to make sure you’re progressing in those areas where you need to improve.”
- Create a data classification policy and identify assets and vendors. “Secure” is a condition that is almost always determined partially by the potential value of the asset you’re trying to secure. “Is Drop Box a place where you’re going to store all your sensitive employee information or clients’ credit card numbers? Absolutely not,” Zusman says. “Is it a great place to store marketing material or large images of a non-sensitive nature? Sure.
“Every organization has to identify its own data assets, classify them (from highly confidential to public, and everything in between), and then come up with some rules for how each class of data can be handled and stored,” Zusman says. “Is Drop Box secure? It depends on your data classification policy.”
- Train users and generate security awareness. More than nine out of ten data security breaches start with an email or other communication designed to trick a company’s network users into giving up their log-in credentials. “Ultimately, training end users specifically to identify and not fall for phishing attacks is very important,” Zusman says.
- Manage your vendors and subcontractors. Use your data classification system to clearly identify the types of information you will trust your vendors and subcontractors to handle. Require vendors who must have high-security data to do their jobs to demonstrate that their own systems are secure. “Know who your vendors are,” Zusman says. “A lot of organizations don’t even have that list of vendors.”
- Consider data breach and cyber liability insurance. The incidence of data theft continues to rise as does the cost. The 2015 Cost of Data Breach Study, multi-industry research commissioned by IBM, found that data breaches cost U.S. companies an average of $217 per data record compromised. Zusman recalls the bind a friend got into when his email-as-a-service business was breached by an adroit phisher who established a firm foothold on their network.
“They paid $70,000 to have incident-response guys come in and figure out what happened – where are these bad guys in the network, what’s the full extent of the breach?” Zusman says. “That $70k was covered by their data-breach cyber liability insurance.”
James Benham, from JBKnowledge, elevates the value of applying for insurance as a good first security step for many firms.
“The underwriting process will force you to essentially go through a free consulting engagement,” Benham says. “To answer all the questions and actually get coverage, you have to comply with all their procedures.
“Cyber liability policy protects you – make sure you get first- and third-party coverage so you’re covered and your clients are covered,” he adds. “It protects you and then it forces you to stay compliant and do a complete security audit.”
Zusman recommends a free resource for organizations getting started in cyber security: the Cybersecurity Framework published by the National Institute of Standards and Technology (NIST). “We started using this with clients to sort of baby-step them through their risk management program.”
And Zusman stresses the need to identify the people inside and outside your company who use your data systems, all of the software that governs your business processes, all of the infrastructure that stores and uses your information, and the security obligations and vulnerabilities that threaten those assets. “Most organizations fail at asset identification,” Zusman says. “That’s why so many organizations have devices and systems exposed to the internet that allow bad guys to hack into their networks.”
Zusman encourages contractors think of data security as a long-term commitment. “Security is a process, not a state,” he says.