Threat factors are numerous and the threat environment has changed over the years. Now more than ever, your company should be prepared with best practices and protocols that computer system administrators and users can undertake to improve cybersecurity.
Good cyber hygiene was the topic of conversation during the Creating Cyber Resilient Future webinar hosted by United for Infrastructure. With the rise in remote work and connected technology, the digital risks are even higher than previous years.
"Threats are evolving", says Kevin Heaslip, PhD., professor Virginia Tech. "It is important to detect abnormalities within a system. If its not working the way it should be, diagnose, mitigate the threat and continue to monitor the system."
Culture of Education
"It is important to create a culture of education within your organization," says Kurt John of Siemens USA. "Make sure to understand the benefits and risks of new technologies, have a strong IT and operational strategy in place."
A good cyber hygiene policy goes across all functions of a company. From a crew leader using their tablet in the field, to the office staff entering payroll into the system. All employees should understand how to protect their digital assets and information. Here are three simple ways to mitigate cybersecurity risks:
- Utilize strong passwords
- Beware of suspicious emails, websites and links
- Keep devices up-to-date
Mark Warner, senator from Virginia says, "Younger people are more candidly comfortable with technology. It is important to have education behind the basic cyber hygiene strategies such as not clicking on a suspicious links. That results in limiting the vulnerability of a system."
Cyber threats are constantly evolving, so it is imperative that your company maintains a resilient system to deter those threats from entering. Practice good cyber hygiene, develop a mitigation strategy and educate all employees across the organization.
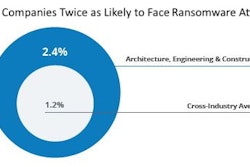
Read Next: AEC Firms are Twice as Likely to Face Ransomware Attacks