Global ransomware damage costs are predicted to hit $20 billion in 2021, up from $11.5 billion in 2019, $5 billion in 2017, and just $325 million in 2015, according to the Cisco/Cybersecurity Ventures 2019 Cybersecurity Almanac.
The U.S. Cybersecurity & Infrastructure Security Agency (CISA) says “Ransomware is an ever-evolving form of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable. Malicious actors then demand ransom in exchange for decryption. Ransomware actors often target and threaten to sell or leak exfiltrated data or authentication information if the ransom is not paid.”
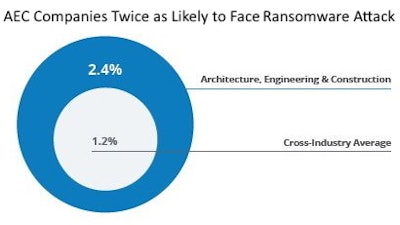
Ransomware threats to the construction industry continue to rise as economic and technological factors make architecture, engineering and construction (AEC) firms prime targets for bad actors. In fact, research by cloud-data-management provider Egnyte reveals that AEC firms are more than twice as likely to suffer ransomware attacks than all other industries.
Egnyte organizes security best practices into identification, containment, eradication and education to harden your network and maintain secure backup that can replace files rather than pay ransom.
Ransomware defense is most difficult at businesses with older PCs, networks, firewalls, or operating systems. Those that don't immediately update to the latest software to “patch” security issues are particularly vulnerable, according to Yuriy Tatarintsev, manager of technical operations at BTI Communications Group, an IT cybersecurity provider. He says even one computer running an older, unsupported version of Windows, for instance, can be “a chink in the defensive armor that invites intrusion."
So the fight against ransomware begins with having a company-wide process to ensure that all machines are patched with the latest security updates from Microsoft and other applications as soon as they are released.
Identification
The faster a ransomware attack can be identified, the easier it is to limit the damage to your organization’s files. That’s why Egnyte recommends all AEC firms should implement these preventive and automated detection capabilities:
- Ensuring they are running up-to-date endpoint detection response to continually monitor and respond to cyber threats
- Establishing an identity access management solution to limit access to specific technologies and files
- Employing a next-gen firewall and zero-day threat detection to intercept first-of-a-kind attacks
- Implementing unusual behavior detection to identify anomalies that could be a ransomware attack
“We recommend a new generation of advanced antivirus software that does not always depend on identifying known threats or ‘signatures,’” says BTI’s Tatarintsev. Such software uses artificial intelligence to analyze which PC programs and processes are affected and as soon malicious activity is detected, stops it
The Best Ransomware Protection for 2021 review by PCmag.com says a well-designed antivirus utility should eliminate ransomware on sight, but black-hat designers work hard to get around both old-school signature-based malware detection and more-flexible modern techniques.
Modern antivirus utilities supplement signature-based detection with some form of behavior monitoring. Behavior-based detection specifically aimed at encryption-related ransomware behaviors is becoming more common.
Ransomware typically goes after files stored in common locations like the desktop and the Documents folder. Some antivirus tools and security suites foil ransomware attacks by denying unauthorized access to these locations. On any access attempt by an unknown program, they ask the user whether to allow access. If that notification comes out of the blue, block it!
Containment
Once a successful attack has been detected the organization needs to move quickly to stop its self-replicating properties and restrict its access to targeted files. This can be realized in two streams, restricting the ransomware’s access to files and restricting the users’ access to files by:
- Ensuring that the trash purge policy is adjusted based on requirements. Egnyte recommends at least 30 days after deletion of data
- Implementing a codified file version policy. Best practice is to retain at least three versions
- Setting a reasonable content retention or lifecycle policy
- Implementing script blocking functionality to restrict the use of cookies
- Installing automatic ransomware notification so administrators can cut off user access in case of a breach
Eradication
When an attack is contained, the next step is to eliminate it from the system by purging any potentially infected files and replacing them with a clean backup. This requires predetermined actions as part of a complete disaster recovery plan, such as:
- Backing up all data with a third-party cloud vendor.
- Enabling selective file restoration to reduce downtime
- Establishing a vetting process for both employees and equipment to reduce the chance of reinfection
- Creating a clean network to run operations until you are sure all ransomware has been eliminated
PCMag.com calls online backup utilities to keep an up-to-date backup of your essential files “the very best defense against ransomware.” Root out offending malware from an infected system, perhaps with help from your antivirus company's tech support, and simply restore your backed-up files.
PCmag.com includes reviews of its ransomware-protection tests and advice on selecting anti-ransomware and antivirus software.
Tatarintsev notes that even with a good backup solution, some data will likely be lost if backups are less than virtually continuous.
Some ransomware attempts to encrypt your backups as well. Take care in transferring and saving backup data, so ransomware does not have access to storage sites connected to company networks. PCmag.com warns that backup systems in which your backed-up files appear in a virtual disk drive may be especially vulnerable.
Education
Egnyte says the most important best practice to prevent ransomware is education. Today, 85% of all breaches involved a human element; which includes phishing, business email compromise, lost or stolen credentials, using insecure credentials, human error, and misuse. And while those will never be eliminated (people are human), education can significantly reduce the likelihood of them occurring. A comprehensive cybersecurity awareness program, formalized, updated, and delivered to all employees on a regular basis will go a long way to preventing a successful ransomware attack.
“Statistically most construction companies acquire ransomware when an employee receives a suspicious email that seems legitimate and clicks on an embedded link. This starts the ransomware attack, which then spreads throughout the company network,” says Tatarintsev.
To protect against this hazard, Tatarintsev recommends construction businesses use advanced email spam protection tools that offer significantly more defensive capability than earlier, more rudimentary options.
“The advanced tools not only filter out all potentially malicious emails, but also stop users from going to dangerous website destinations by clicking on links that could start a ransomware attack,” he says. He explains that the tools rewrite all the embedded link Uniform Resource Locators (URLs). So, if a user clicks a URL in an email, instead of linking to a potentially dangerous website, he or she is redirected to a safe location or ‘sandbox.’ The URL is analyzed to determine if it is dangerous, and if it is safe the user is allowed to go to the original website destination.
Since deceptive “phishing” emails designed to start a ransomware attack can appear so similar to authentic emails, Tatarintsev advises that security-awareness training programs include periodic testing that includes sending safe, simulated phishing emails to test employees’ responses. Employees who fall for the phishing lures should be given additional training, so they will not compromise the business when an actual email-ransomware assault is attempted.
Ready to call in a pro?
The ranks of ransomware designers include technically advanced professional criminals whose only job is defeating network security. If your IT department isn’t staffed up, trained and funded, the services of a cloud security firm like Egnyte or third-party security firms like BTI can safeguard your operating data cost effectively. They also minimizes potential loss, and even liability, if serious harm were to be caused by disrupted company services.
Service providers are also ransomware targets. Tatarintsev says the first and primary goal of a third-party, integrated IT service is to deliver the foremost level of technical quality that can be delivered reliably for a client’s budget.
“We emphasize the quality and reliability aspects. Where cybersecurity is concerned, any other approach, no matter how seemingly cost beneficial, can be fatal. By putting quality first before short term economic advantage from cheaper tools, we and our clients end up winning in the end.”
Only carefully selected software tools and technical solutions should be utilized to ensure its clients are always operating in a high-performance, reliable, and secure IT environment.
“Our persistent threat monitoring and prevention tools identify root causes of threats, reverse malicious attempts in the early stages, and prevent incidents from penetrating our client systems,” says Tatarintsev. “Our 24/7 Security Operating Center provides managed detection and response by continuously watching the environments and reacting rapidly to potential risks, ensuring ongoing protection with the most current security insights and guidance available.”
Egnyte says there are two types of companies: those who have been attacked by ransomware and those that will be attacked. A comprehensive program that starts with identifying your most critical content is required to prepare for a ransomware attack and be sure your firm can mitigate the impact and get operations up and running as soon as possible.